
Diving deep into TrustZone – Enhancing security in embedded systems
The embedded industry is rapidly evolving, and with it, robust, secure, and efficient microcontrollers are needed. Enter Armv8-M architecture—the latest leap forward in the Cortex-M family. Throughout a three-part blog series, we’re exploring the new features and improvements introduced in Cortex-M23 and Cortex-M33 microcontrollers, designed to address modern challenges in embedded systems.
In previous posts, we've covered:
Part 1: The new C11 language support and significant MPU (Memory Protection Unit) updates. These enhancements are critical for ensuring data integrity and memory security, key components of any robust embedded system.
Part 2: Focus on performance improvements in Cortex-M0/M0+, such as adding hardware division, long branch instructions, and more efficient MOV operations. These updates give developers a performance edge while maintaining low power consumption.
In this final part, we’ll wrap up by taking a closer look at security improvements. With embedded devices increasingly connected to networks, TrustZone technology and stack protection have become essential for safeguarding systems from threats. We’ll explore how these features enhance security.
Whether you’re designing for industrial automation, IoT, or safety-critical applications, this series will give you valuable insights into how Armv8-M shapes the future of embedded systems.
Part 3: Diving deep into TrustZone – Enhancing security in embedded systems
In today's connected world, embedded devices are vulnerable to security threats. Whether through wireless or wired connections, embedded systems are potential targets for malicious activities, such as system shutdowns, software manipulation, or even full-blown system hijacking. That’s why security is no longer optional—it’s essential.
Enter Armv8-M. This architecture brings much-needed security features to the embedded space, with two significant improvements:
• TrustZone Security
• Stack Protection
Let’s break down how these features are raising the bar for security in embedded systems.
TrustZone: The game-changer for security
One of the most exciting additions to Armv8-M is TrustZone, a technology that separates a system into two distinct states: Secure and Non-Secure. These states are designed to keep critical operations isolated from less reliable ones, ensuring that sensitive data and functions remain protected.
Here’s how it works:
• Secure state: This state runs trusted, secure programs.
• Non-Secure state: This state runs less trusted, potentially vulnerable programs.
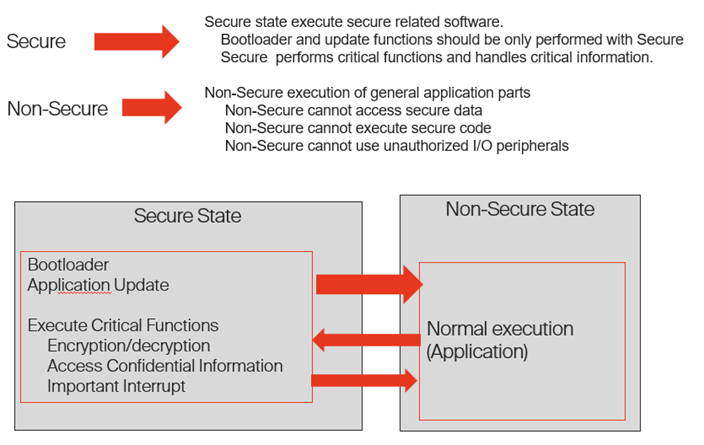
These two states operate independently, but they can still communicate through shared memory. The secret to TrustZone’s security is that the Non-Secure state has no access to data in the Secure state unless it is explicitly allowed.
How does TrustZone handle memory?
TrustZone allows you to assign different sections of Flash and RAM to Secure, Non-Secure, or Non-Secure Callable (NSC) areas. By setting these restrictions, you can control which parts of the system are accessible based on the state.

Function calls: Transitioning between Secure and Non-Secure states


The important part? The Non-Secure side doesn’t need to worry about TrustZone—it just runs as it normally would. The Secure side takes care of making sure everything stays… well, secure.
Calling secure functions from Non-Secure code
The process for calling a Secure function from a Non-Secure program is just as simple. The Non-Secure code jumps to a special NSC (Non-Secure Callable) area, where the secure function is executed. Once the secure operation is complete, the BXNS instruction sends the program back to Non-Secure mode, where it continues normal execution.

What’s key here is that even if attackers compromise the Non-Secure side, TrustZone ensures they can’t easily access or manipulate Secure functions.
Stack protection: Guarding against overflows
Security threats aren’t limited to data theft—some attacks exploit stack overflows to crash systems or hijack control. That’s why Armv8-M introduces Stack Protection, a simple but effective feature.
By setting stack limits using PSPLIM and MSPLIM, the system raises an exception if the stack overflows. This helps prevent stack overflow attacks, a common method hackers use to execute malicious code.

In the event of a stack overflow, the system triggers a UsageFault exception, helping you quickly identify and address the issue.

Security: More critical than ever
Security standards like ISO/SAE 21434, ISO 24089, and IEC 62443 are increasingly relevant in the embedded world. TrustZone and other security measures from Armv8-M are designed to meet these rigorous standards, ensuring your embedded systems are prepared for the future.
However, just having TrustZone isn’t enough. Broader security strategies are also essential to protect against threats like data theft, password breaches, and software tampering. That’s where tools like IAR Embedded Trust come in. The included secure boot manager simplifies security without the need to master every detail of TrustZone implementation.
Summary: The importance of embedded security
As embedded systems continue to evolve, security becomes even more critical. Armv8-M’s TrustZone and Stack Protection features are vital in creating secure, reliable embedded systems. Tools like the IAR Embedded Workbench and IAR Embedded Trust make it easier to harness these security features and build systems that meet modern security standards.
When selecting your next microcontroller, look beyond performance to ensure you’re equipped with the right tools to build secure systems from the ground up.
Take the next step
Equip your embedded projects with the latest in performance and security capabilities. Download the evaluation version of IAR Embedded Workbench for Arm to try Cortex-M23 and Cortex-M33 support.
For security features, request a demo of IAR Embedded Trust to see how it handles secure boot and TrustZone.

