
Solution
Embedded security
Trusted device security with IAR


Regulatory compliance and cybersecurity assurance

The 4A's: A layered approach to embedded security
Simplifying embedded security from development to production
Security is no longer optional—embedded systems must meet strict industry regulations. Ensuring firmware integrity with secure boot, encryption, and IP protection is key to protecting intellectual property, preventing firmware manipulation, and maintaining system reliability.
Security starts with code quality. Enforcing SEI CERT C coding standards, along with static and runtime analysis, reduces vulnerabilities, strengthens software security, and minimizes attack surfaces. A shift-left approach with DevSecOps integrates security early in development, identifying issues before they become critical and ensuring compliance with industry regulations, security legislation, and the EU Cyber Resilience Act.
The 4A’s: Core security principles for embedded systems
Authentication verifies device identity and prevents unauthorized access. Active IP protection safeguards software from theft and misuse. Anti-rollback and secure updates ensure only verified firmware is installed, blocking outdated versions. Anti-cloning prevents counterfeit devices from running unauthorized software.
End-to-end embedded security with IAR’s solutions
IAR’s security solutions provide comprehensive protection across development and production. IAR Embedded Trust enforces security in new designs, while IAR Embedded Secure IP enhances protection for existing projects. IAR Secure Deploy safeguards provisioning, preventing overproduction and unauthorized access. Seamlessly integrated into DevOps workflows, IAR’s security framework automates validation, strengthens compliance, and secures both non-connected and IoT-enabled systems.

Explore IAR’s embedded security components
Ensure firmware integrity with secure boot, encryption, and IP protection, preventing unauthorized access, protecting intellectual property, and maintaining system reliability throughout the product lifecycle.
Product
IAR Embedded Trust
Provides a secure development framework with encryption, secure boot, and device authentication for embedded systems.
Product
IAR Embedded Secure IP
Safeguards embedded IP from cloning, tampering, and unauthorized access with strong encryption and device authentication.
Product
IAR Secure Deploy
Protects firmware during production with IP protection, anti-cloning measures, and secure provisioning workflows.
Product
IAR Embedded Workbench
Complete toolchain with an industry-leading compiler, debugger, and analysis tools, ensuring efficient, high-performance embedded development.
Product
IAR C-STAT
Detects defects, security vulnerabilities, and compliance issues early with powerful static analysis for MISRA C/C++, CERT C/C++, and industry standards
Product
IAR Build Tools
Automates builds and testing in CI/CD pipelines with high-performance command-line tools, enabling scalable cloud and on-prem workflows.
Product
IAR C-RUN
Identifies runtime errors, memory leaks, and overflows, improving software reliability and debugging efficiency.
Features
Trusted security for embedded software compliance
Secure boot and key provisioning
Ensures only authenticated firmware runs, protecting against malware and unauthorized code modifications.
Encryption and IP protection
Secures firmware from reverse engineering, unauthorized access, and software theft.
Secure firmware updates
Prevents rollback attacks, ensuring only verified updates are installed, maintaining long-term device security.
Dynamic application security testing (DAST)
Analyzes executed code in real-world conditions to detect runtime vulnerabilities.
Static application security testing (SAST)
Detects security flaws, enforces best practices, and ensures code maintainability early in development.
End-to-end security enforcement
Covers development, pre-production, volume production, and operational life for long-term protection.
Shift-left security and automated testing
Integrates security early in the development process, reducing vulnerabilities before deployment.
Customer stories
Transforming challenges into success
Casio — Improving time to market
Read caseAlthough we increased performance, we also had to maintain power consumption, which is why we divided processing into two cores. It was a lot of work, but we were able to find a balance between improved performance and power efficiency.
Osong Medical Innovation Foundation – Ensuring medical software certification
Read caseQuality and certification are critical for the future of high-tech medical devices. By using C-STAT, we can improve code quality while preparing for IEC 62304-certified functional safety upgrades to meet regulatory standards.
NEWGIN – Strengthening software quality for the future
Read caseAs firmware complexity grows, we see an increasing need for tools that help ensure software quality. Static analysis and CI tool integration will be key to improving reliability and maintaining high standards in development.
VICTEK – High-quality code for secure IoT systems
Read caseDeveloping low-power IoT systems requires defect-free, high-quality code to ensure secure integration with optimized applications and networks, while minimizing cybersecurity risks.
Landis+Gyr – Early bug detection with static analysis
Read caseTo maintain high product quality, we need tools that catch defects early in development. C-STAT allows us to find bugs faster, reduce time to market, and streamline development costs, making it a core tool across our sites.
Our featured blog posts
FAQ
How can secure boot and key provisioning protect our firmware from unauthorized modifications?
Secure boot ensures only authenticated firmware runs on a device, protecting it from unauthorized modifications.
What are the best practices for implementing secure firmware updates in connected devices?
Best practices for secure firmware updates include encryption, authentication, and rollback protection to prevent security breaches.
How does compliance with the EU Cyber Resilience Act impact embedded security design?
Compliance with the EU Cyber Resilience Act ensures embedded devices meet the latest cybersecurity regulations.
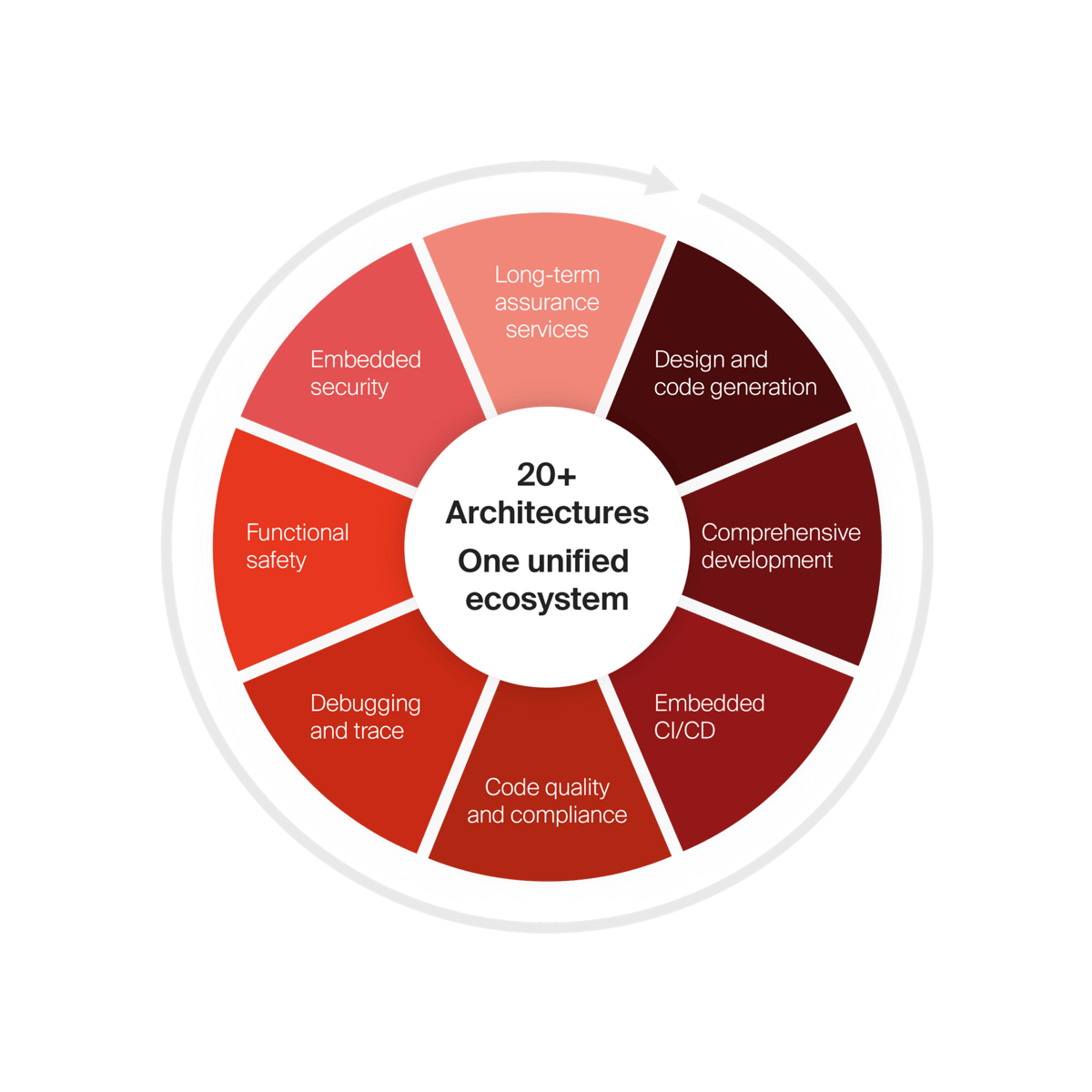
IAR embedded development platform
Get access to all
Scale development operations with freedom and flexibility, accelerate innovation with code confidence and simplify compliance while strengthening security.
- Architecture and device agnostic
- Cloud-ready, tailored for enterprises
- Functional safety always included
- End-to-end embedded security
With our platform, you get access to everything.





